ISO Flashcards
ISO family

IOS faimly 2 27007-onwards

IOS 27001 family 3 27015-onwards

ISO 27001 family 4 27023

IOS family5

IOS family 6

PIM controls

Interested parties

Asset 8

example compliance policy

A18.2.3 Tech Complinace Review

A18.2.2 Compliance with Sec & Standards

A18.2.1 Independent Review of info Sec

A.18.1.4 Privacy & Protect of personally ID info

A18.1.3 Protection of Records

A.18.1.2 Intellectual Property rights

A.18 Compliance (2)

A.18 Compliance

Key in InfoSec Continuinty

A17.1.3 Verify review & Evaluate INfo Sec Continuity

PDCA

Threat, Risk , Vulnerability

Sec Measures

Incident cycle
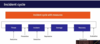
Incident cycle T,R,V

C,i,A & Correctness

owner of asset

worm, Spyware

ISMS CSF

ISMS CSF 3.6 reflect

wheel

Annex A IS Ctrl Cat

Project Progression

A18 Compliance

A18 Compliance breakdown

A18.2

ISMS

A.12 Ops Sec

A.12 Ops Sec p2

A12.2. Ops Sec

A12.4 Ops Sec

A12.5,6,7 Ops Sec

A13 Comms Sec

A13.2 Comms Sec

A14 Sys Acquisition Dev & Maintence

A14.2 Sys Acq ,dev, Maintence

A14.2. X Sys Acq, Dev, Main

A.15 Supplier Relationships

A16 IS inc Mgmt

A16.1 IS Inc Mgmt

A16. IS Inc mgmt Lifecycle

A17 IS Aspect of BC mgmt

A10 Cyprto

A11 Physical & Env Sec

A11.1 Phy & Env Sec

A11.2.3- Phy Env Sec

A8 Asset Mgmt

A.8.1.2- Asset Mgmt

A.8.2 Asset Mgmt

A.8.3 Asset Mgmt

ISC Access Ctrl A9

A.9 Access Ctrl

A.9 Access Ctrl

A.9.4 Access Ctrl

A.94..4 & 5. Access Ctrl

A.& HR Sec

A7.1 HR Sec

A7.2 HR Sec

A7.3 HR Sec

HR Sec A7 example

A.& HR Answer

8.1 Ops

8.1 Ops outsource

8.1 Ops

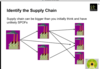
Supply Chain Rish Mgmt

Id supply Chain

ID supply Chain
Common failing in Deployment

Ops steps for Effective Deployment

risk Assessment 8.2 & risk treatment

Annex A ref cntrl Obj & contrl

A.6 Org of IS

A6.1.4&5 Org of IS

A6.2. Org of IS

ISC Org of IS

6.1 Planning

IS Obj 6.2

IS Obj 6.2 part 2

measuring effectiveness

ISMS obj & Measurement

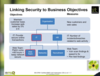
Link Sec to Bus Obj
Risk Treatment

Risk Assessement Ex- Impact Scale

Clause 6 Planning 6.1

Risk Decision

Options for Risk Decision

Risk Treatment - Risk Acceptance Criteria

ctrl

ex ctrl PPP

Risk & countermeasure- Likeihood impact

ISMS Risk Treatmemt

Compare ctrl to annex A

SOA detail security design

SOA Ex

SOA Manual- Procedure - Forms -records

ctrl listing handout

Risk Mgmt spreadsheet

Risk Assessment tool

Risk Mgmt Summary

Risk Mgmt Summary

Cont Improvement

clause 6.2 Planning

6.1.2 assess IS risk

IS risk Ass 6.1.2

Conduct Risk Ass 2 appraoch

Detail of Risk mgmt- High level- Detais

ISO27005 Risk Mgmt

Risk Assessmet - ID risk

Risk Scenarios- componets

NIST Risk Mgmt framework

Info Assurance Standard

Octava

Asset-based risk mgmt
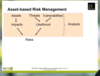
Asset-based risk - treatment

Risk Asset ex

Risk Assessment Ex Y

Risk Assessment Ex Y

determining impact Value

Risk Criteria

stage 1 intent audit

stage 2 implementation Audit

Audit Obj

if NC found

most common problem at Audit - Risk Mgmt

Most common Problem at Audit- Misc

ISMS should not stop evolving in prep for Audit

Clause 9- Performance Eval

perofrmance eval 9 - orgs and focus

data collection tech

Mgmt Process - Maturity framework

performance eval- understanding and acceptance

performance eval- reporting on Polcy Deployment

perforamance eval- reporting on polciy deployment

clause 9- performance Eval 9.1,2,3

IS Standard- auditing apps

Monitoring and mgmt internal audit 1st party

auditing mgmt Sys Obj

monitoring & mgmt - conducting interal Audits

performance eval- After internal Audit

mgmt review 9.3

mgmt review 9.3 part 2

clause 4 - context

clause 4.1

4.2 interesting parties

e.g interested party

4.3 determine scope

scope

trust boundaries on the cloud

context & leadership

clause 5 - leadership

clause 5 - leadership

selling IS & ISO 27001

selling IS & ISO part 2

5.1 Leadership

5.1 Leadership part 2

- Policy

ISC IS Policy A5

ISC IS Polices A5 eg

IS Policies A5 - Obj

5.3 Roles and Responsibilities

Info Mgmt

confidentiality

Integrity

Integrity

available measure eg.

Parkerian hexad

threat & threat agent

human threats

non human threats

Risk

threat & risk

vulneraability

Exposure

threat & threat agent

human threats 2

Risk analysis

risk strategies

countermeasures

categories of countermeasures

countermeasure - prevention

countermeasure - reduction

countermeasure- detection

countermeasure - repression

countermeasure- acceptance

due care

sec measures - chart
ISMS PDCA

ISMS framework

sec policy

sec policy contents

obj & the content of sec org

ISMS framework domains

IS roles

obj chart of Sec org

logical access ctrl




















































































































































































































































































































