Chapter 2: Data Handling Ethics Flashcards
To master concepts and content from DMBoK 2 Chapter 2: Data Handling Ethics toward CDMP certification (49 cards)
What is the DMBoK definition of ethics?

Ethics are principles of behavior based on ideas of right and wrong.

Name at least four of the eight example ideas on which ethical principles are focused.

Ethical principles often focus on ideas such as fairness, respect, responsibility, integrity, quality, reliability, transparency, and trust.

What is the DMBoK definition of data handling ethics?

Data handling ethics are concerned with how to procure, store, manage, use, and dispose of data in ways that are aligned with ethical principles.

What are four reasons that DAMA says that data handling ethics are important?

1) Handling data in an ethical manner is necessary to the long-term success of any organization that wants to get value from its data. 2) Unethical data handling can result in the loss of reputation and customers, because it puts at risk people whose data is exposed. 3) In some cases, unethical practices are also illegal. 4) Ultimately, for data management professionals and the organizations for which they work, data ethics are a matter of social responsibility.

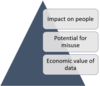
List three core concepts of data handling ethics from the DMBoK.

1) Impact on people: Because data represents characteristics of individuals and is used to make decisions that affect people’s lives, there is an imperative to manage its quality and reliability. 2) Potential for misuse: Misusing data can negatively affect people and organizations, so there is an ethical imperative to prevent the misuse of data. 3) Economic value of data: Data has economic value. Ethics of data ownership should determine how that value can be accessed and by whom.
Which one of these five goals is NOT in the DMBoK as a business driver for data handling ethics?

1) To define ethical handling of data in the organization
2) To educate staff on the organizational risks of improper data handling
3) To change/instill preferred culture and behavior on handling data
4) To streamline and automate data handling in accordance with data ethics
5) To monitor regulatory environment, measure, monitor, and adjust organizational approaches

Name at least three of the six inputs needed to define data handling ethics for an organization.

1) Existing and preferred organizational ethics 2) Business Strategy and Goals 3) Organizational Structure 4) Business Culture 5) Regulations 6) Existing Corporate Policies

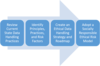
What are the six core activities of data handling ethics?
1) Review Data Handling Practices
2) Identify Principles, Practices, and Risk Factors
3) Create an Ethical Data Handling Strategy
4) Address Practice Gaps
5) Communicate and Educate Staff
6) Monitor and Maintain Alignment

Name at least five of the nine deliverables that the DMBoK recommends for a data handling ethics program.

1) Current Practices and Gaps 2) Ethical Data Handling Strategy 3) Communication Plan 4) Ethics Training Program 5) Ethical Corporate Statements 6) Awareness of Ethical Data Issues 7) Aligned Incentives, KPIs, and Targets 8) Updated Policies 9) Ethical Data Handling Reporting

Name at least three of the six key stakeholders needed to supply the inputs to an ethical data handling program

1) Executives 2) Data Stewards 3) Executive Data Stewards 4) IT Executives 5) Data Providers 6) Regulators

Name at least four of the seven key stakeholders needed to conduct the activities of an ethical data handling program

1) Data Governance Bodies 2) CDO/CIO 3) Executives 4) Coordinating Data Stewards 5) Subject Matter Experts 6) Change Managers 7) Data Management Services

Name the three key stakeholders recommended as consumers of an ethical data handling program
1) Employees 2) Executives 3) Regulators

List four core techniques and tools used as technical drivers for a data handling ethics program

TECHNIQUES Communication Plan Checklists Annual Ethics Statement Affirmation TOOLS Wikis, knowledgebases, intranet sites Microblogs, other internal communications tools

List three key metrics of a successful ethical data handling program

1) Number of employees trained
2) Compliance/noncompliance incidents
3) Corporate executive involvement

What are two assumptions that lead organizations to fail at data ethics, and two trends that make it important to succeed?
Unfortunately, many organizations fail to recognize and respond to the ethical obligations inherent in data management. They may adopt a traditional technical perspective and profess not to understand the data; or they assume that if they follow the letter of the law, they have no risk related to data handling. This is a dangerous assumption. The data environment is evolving rapidly. Organizations are using data in ways they would not have imagined even a few years ago. While laws codify some ethical principles, legislation cannot keep up with the risks associated with evolution of the data environment. Organizations must recognize and respond to their ethical obligation to protect data entrusted to them by fostering and sustaining a culture that values the ethical handling of information.

What are five key business drivers (opportunities and threats) that motivate an organization toward a data ethics program?

OPPORTUNITIES Like W. Edward Deming’s statements on quality, ethics means “doing it right when no one is looking.” An ethical approach to data use is increasingly being recognized as a competitive business advantage (Hasselbalch and Tranberg, 2016). Ethical data handling can increase the trustworthiness of an organization and the organization’s data and process outcomes. This can create better relationships between the organization and its stakeholders. THREATS Data handling doesn’t happen in a vacuum, and customers and stakeholders expect ethical behavior and outcomes from businesses and their data processes. Reducing the risk that data for which the organization is responsible will be misused by employees, customers, or partners is a primary reason for an organization to cultivate ethical principles for data handling. There is also an ethical responsibility to secure data from criminals (i.e., to protect against hacking and potential data breaches).

What is entailed in creating an ethical culture for data handling?
Creating an ethical culture entails introducing proper governance, including institution of controls to ensure that both intended and resulting outcomes of data processing are ethical and do not violate trust or infringe on human dignity.

How does data ownership influence data handling ethics?

Different models of data ownership influence the ethics of data handling. For example, technology has improved the ability of organizations to share data with each other. This ability means organizations need to make ethical decisions about their responsibility for sharing data that does not belong to them.

Name five emerging roles and responsibilities for data handling ethics

The emerging roles of Chief Data Officer, Chief Risk Officer, Chief Privacy Officer, and Chief Analytics Officer are focused on controlling risk by establishing acceptable practices for data handling. But responsibility extends beyond people in these roles. Handling data ethically requires organization-wide recognition of the risks associated with misuse of data and organizational commitment to handling data based on principles that protect individuals and respect the imperatives related to data ownership.
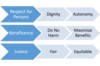
Name and define three tenets of bioethics that provide a starting point for principles of data ethics

Respect for Persons: This principle reflects the fundamental ethical requirement that people be treated in a way that respects their dignity and autonomy as human individuals. It also requires that in cases where people have ‘diminished autonomy’, extra care be taken to protect their dignity and rights. Beneficence: This principle has two elements: first, do not harm; second, maximize possible benefits and minimize possible harms. Justice: This principle considers the fair and equitable treatment of people.
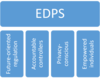
List the European Data Protection Supervisor’s four pillars required for an information ecosystem that ensures ethical treatment of data

- Future-oriented regulation of data processing and respect for the rights to privacy and to data protection
- Accountable controllers who determine personal information processing
- Privacy-conscious engineering and design of data processing products and services
- Empowered individuals
What are the seven principles of the General Data Protection Regulation of the EU (GDPR)?

1) Lawfulness, fairness, and transparency 2) Purpose limitation 3) Data minimization 4) Accuracy 5) Storage limitation 6) Integrity and confidentiality (security) 7) Accountability

Name at least five of the ten statutory obligations of the Canadian privacy law PIPEDA (Personal Information Protection and Electronic Documents Act)
1) Accountability 2) Identifying purposes 3) Consent 4) Limiting collection 5) Limiting Use, Disclosure, and Retention 6) Accuracy 7) Safeguards 8) Openness 9) Individual access 10) Challenging compliance

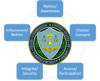
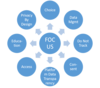
What are the five Fair Information Processing Principles recommended by the US Federal Trade Commission (FTC)?

1) Notice/Awareness 2) Choice/Consent 3) Access/Participation 4) Integrity/Security 5) Enforcement/Redress