Ch 24: Network Assurance Flashcards
(25 cards)
What is the default Hello timer and Dead Interval for OSPF for these network types:
- Broadcast
- Non-broadcast
- Pt to Pt
- Pt to MultiPoint
The network types need to match in order to form adjacencies.

Write the commands to debug ip packets but only include packets to and from the subnet 192.168.14.0/24.
R4(config)# access-list 100 permit ip any 192.168.14.0 0.0.0.255
R4(config)# access-list 100 permit ip 192.168.14.0 0.0.0.255 any
R4# debug ip packet 100
This showcases the power of conditional debugging, This creates a standard access list to limit the messages to the console and filter solely on traffic to and from the 192.168.14.0/24 subnet.
logging buffer 7
logging buffer 100000
What do these commands accomplish?
This will set the logging level to the most verbose, sharing all debug level messages with syslog and setting the buffer size to 10000

What is the command to show the logging information stored locally.
show logging
This will show both the configuration and the stored logs.
What is the command to send the logs to a host at 192.168.14.100 and set the level to record errors and other events more serious than errors.
logging host 192.168.14.100
logging trap 3
This will record logging levels 0-3, emergencies, alerts, critrical, and errors.
NetFlow has two components that must be configured: ______________________ and ______________________.
NetFlow has two components that must be configured: NetFlow Data Capture and NetFlow Data Export.
NetFlow Data Capture captures the traffic statistics.
NetFlow Data Export exports the statistical data to a NetFlow collector, such as Cisco DNA Center or Cisco Prime Infrastructure.
What is a flow in NetFlow?
NetFlow collects traffic based on flows. A flow is a unidirectional traffic stream that contains a combination of the following key fields:
- Source IP address
- Destination IP address
- Source port number
- Destination port number
- Layer 3 protocol type
- Type of service (ToS)
- Input logical interface
What commands are required for configuring R1’s Ethernet0/1 interface for NetFlow Data Capture and exporting the data to the 192.168.14.100 collector?
R1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)# ip flow-export version 9
R1(config)# ip flow-export destination 192.168.14.100 9999
R1(config)# interface Ethernet0/1
R1(config-if)# ip flow ingress
R1(config-if)# ip flow egress
R1(config-if)# end
R1#
NOTE: 9999 = UDP port
What command will show the interfaces that are configured for NetFlow?
show ip flow interface - which shows the interfaces that are configured for NetFlow.

What command shows the destination for the NetFlow data to be exported to as well as statistics on the export, including any errors that may arise.
show ip flow export - command which shows the destination for the NetFlow data to be exported to as well as statistics on the export, including any errors that may arise.

What command shows the traffic flows that NetFlow is capturing/cacheing?
show ip cache flow - command shows the traffic flows that NetFlow is capturing.

What is the command to show the hosts using the most bandwidth?
show ip flow top-talkers
Another great option for NetFlow is being able to configure the top specified number of talkers on the network. A very useful and quick configuration allows you to gain a great snapshot of what is going on in a device from a flow perspective.
This view can be enabled by issuing the global configuration mode command:
- ip flow-top-talkers
You can configure the top command for the number of talkers (1–200) and the sort-by command to sort by bytes or packets, depending on the use case.
Example 24-39 shows the configuration steps on R1 and the associated verification steps.

What are these? What layers do they operate at?
- Local Switched Port Analyzer:
- Remote Switched Port Analyzer (RSPAN):
- Encapsulated Remote Switched Port Analyzer (ERSPAN):
Local Switched Port Analyzer: You can capture local network traffic on a switch and send a copy of the network traffic to a local port attached to some sort of traffic analyzer connected to a port on the same switch.
Remote Switched Port Analyzer (RSPAN): You can capture network traffic on a remote switch and send a copy of the network traffic to the local switch through Layer 2 toward a local port attached to some sort of traffic analyzer.
Encapsulated Remote Switched Port Analyzer (ERSPAN): You can capture network traffic on a remote device and send the traffic to the local system through Layer 3 (routing possible) toward a local port attached to some sort of traffic analyzer.
What are the three sources for a local SPAN session to capture traffic from?
- One or more specific switch ports
- A port channel (also known as an EtherChannel)
- A VLAN (To be more explicit, this is the traffic received by the switch for hosts all the hosts associated to the VLAN specified. This does not include a SVI interface.)
T/F: The source port can be reused between two different SPAN sessions.
False.
The source port cannot be reused between two different SPAN sessions.
T/F: Source ports can be switched ports, L3 ports are not supported.
False.
Source ports can be switched or routed ports.
What is the command to specify a source port in a SPAN session?
The source ports are defined with the global configuration command:
monitor session session-id source {interface interface-id | vlan vlan-id} [rx | tx | both].
The SPAN session-id allows for the switch to correlate the source ports to specific destination ports.
One or more interfaces or VLANs can be entered by using either a comma (for delimiting multiple interfaces) or a hyphen (for setting a range). Another option is to repeat the command with a different value and let the system update the source range accordingly.
The direction of the traffic can be specified as part of the configuration. With the optional rx keyword you capture only traffic received on that source, with the optional tx keyword you capture traffic sent by that source, and with the both keyword you capture all traffic. By default, traffic is captured for both.
You can specify a trunk port as a source port to capture traffic for all VLANs that traverse that port. This might provide too much data and add noise to the traffic analysis tool. The VLANs can be filtered on the capture with the command monitor session session-id filter vlan vlan-range.
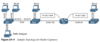
See attached diagram. What are the commands needed to monitor both PC-A’s and PC-B’s communication on SW1 and send it toward the local traffic analyzer? (This is a local SPAN.)

SW1(config)# monitor session 1 source interface gi1/0/1 - 2
SW1(config)# monitor session 1 destination interface gi1/0/9
What is the command to view the SPAN session information?
The session information can be viewed with the command:
show monitor session {session-id [detail] | local [detail]}.
A specific SPAN session can be viewed, or the output can be restricted to the local SPAN session, as shown in Example 24-46.

What commands need to be issued on SW1 to configurte monitoring the trunk port Gi1/0/10 and provide the output to PC-B for PC-A and PC-B communication on SW1 and sending it toward the local traffic analyzer?
The source port is a trunk port, and it is important to restrict traffic to VLAN 123 and capture Layer 2 QoS markings.
The next example illustrates monitoring the trunk port Gi1/0/10 and provides the output to PC-B for PC-A and PC-B communication on SW1 and sending it toward the local traffic analyzer. The source port is a trunk port, and it is important to restrict traffic to VLAN 123 and capture Layer 2 QoS markings.
Example 24-47 shows the commands that are entered on SW1 and then shows the configuration verified by examining the SPAN session.

What VLAN does RSPAN traffic travel over.
The RSPAN function allows the source ports to be located on one switch and the destination port on a different switch. The mirror traffic is placed on a special VLAN called the RSPAN VLAN, which is designated for SPAN traffic only.
A switch with the RSPAN VLAN operates differently from a typical switch:
MAC addresses are not learned on ports associated with the RSPAN VLAN. This ensures that the switch does not try to use the port associated with the RSPAN VLAN to transmit data to the end host, which in turn ensures that the normal forwarding path is maintained.
Traffic is flooded out all the ports associated to the RSPAN VLAN. The RSPAN VLAN should not be associated with ports that are not trunk ports between the source and destination switches.
How is RSPAN configured?
The configuration for RSPAN is straightforward: A VLAN is created and then identified as an RSPAN VLAN with the command remote-span.
The VLAN needs to be the same on all switches for that RSPAN session. Example 24-49 shows the RSPAN VLAN being created on SW1 and SW2.
These two commands will then configure the RSPAN session on the souce port switch:
- SW2(config)# monitor session 1 source interface gi1/0/3
- SW2(config)# monitor session 1 destination remote vlan 99
Note: On the source port switch, the source ports are selected just as explained earlier for local SPAN. However, the destination is the RSPAN VLAN, which is set with the command
- monitor session session-id destination remote vlan rspanvlan-id.
While the session-id is locally significant, keeping it the same on both the source and destination switches prevents confusion.

T/F: A source and destination must be configured for ERSPAN.
True.
To configure a source, the following command is issued:
- monitor session span-session-number type erspan-source
This defines the session number as well as the session type, erspan-source.
Once the initial session is created, the source must be defined in the session. This is accomplished by issuing the command:
- source {interface type number | vlan vlan-ID } [, | - | both | rx | tx] command.
When all these settings have been configured, the session must be enabled with the no shutdown command to ensure that the session is active.
See attached image for a complete ERSPAN config.

What are the commands to configure an IP SLA with these parameters:
- use SLA number 1
- use ping to test
- test 192.168.14.100
- source SLA from L0
- test every 5 minutes
- run test forever
R1(config)# ip sla 1
R1(config-ip-sla)# icmp-echo 192.168.14.100 source-interface Loopback0
R1(config-ip-sla-echo)# frequency 300
R1(config-ip-sla-echo)# end
R1(config)# ip sla schedule 1 life forever start-time now
R1(config)# do show ip sla configuration 1




